This document analyzes the information given in the Microsoft bulletin regarding the Security patch that needs to be applied in all SQL Servers version 7 and above.
Scope of the Document:
1. Information regarding the Bulletin
2. Are we affected?
3. Deployment Plans and Guidance
4. Other points to ponder
Bulletin Information:
Bulletin URL: http://www.microsoft.com/technet/security/bulletin/MS08-040.mspx
http://support.microsoft.com/kb/941203#appliesto
Software Affected: SQL Server 7, 2000 and 2005 (32 bit and 64 bit) and (GDR and QFE releases)
The bulletin describes that a security patch has been released for known vulnerabilities in SQL Server and its components. The known vulnerabilities are listed below.
Memory Page Reuse Vulnerability - CVE-2008-0085
Convert Buffer Overrun - CVE-2008-0086
SQL Server Memory Corruption Vulnerability - CVE-2008-0107
SQL Server Buffer Overrun Vulnerability - CVE-2008-0106
Memory Page Reuse Vulnerability:
With this vulnerability, a database user with access can read other user’s data with custom applications as SQL Server does not initialize the memory pages before reallocating memory to users.
Microsoft has not received any information from customers or other users stating that their system is exploited using this vulnerability and information regarding this vulnerability was brought up through responsible disclosure.
Installing this security path creates a new system stored procedure sp_clean_db_free_space that can be used to clear the residual pages in the memory. This procedure cleans up all files in the database.
Mitigation Factor: Only users with database access can exploit this vulnerability.
Any other Workarounds:
Microsoft Suggests to have the configuration option “Common Criteria Compliance” set to 1. But enabling this option would result in performance degradation of the system and application.
Memory Page Reuse Vulnerability - CVE-2008-0085
Convert Buffer Overrun - CVE-2008-0086
SQL Server Memory Corruption Vulnerability - CVE-2008-0107
SQL Server Buffer Overrun Vulnerability - CVE-2008-0106
Memory Page Reuse Vulnerability:
With this vulnerability, a database user with access can read other user’s data with custom applications as SQL Server does not initialize the memory pages before reallocating memory to users.
Microsoft has not received any information from customers or other users stating that their system is exploited using this vulnerability and information regarding this vulnerability was brought up through responsible disclosure.
Installing this security path creates a new system stored procedure sp_clean_db_free_space that can be used to clear the residual pages in the memory. This procedure cleans up all files in the database.
Mitigation Factor: Only users with database access can exploit this vulnerability.
Any other Workarounds:
Microsoft Suggests to have the configuration option “Common Criteria Compliance” set to 1. But enabling this option would result in performance degradation of the system and application.
Convert Buffer Overrun Vulnerability:
This vulnerability exists in SQL convert function that allows authenticated user to gain elevated control over the system.
Microsoft has not received any information from customers or other users stating that their system is exploited using this vulnerability and information regarding this vulnerability was brought up through responsible disclosure.
Mitigation Factor: Only users with database access can exploit this vulnerability.
Any other Workarounds: None
SQL Server Memory Corruption Vulnerability:
This vulnerability exists in SQL server that allows authenticated user to gain elevated control over the system.
Microsoft has not received any information from customers or other users stating that their system is exploited using this vulnerability and information regarding this vulnerability was brought up through responsible disclosure.
Mitigation Factor: Only users with database access can exploit this vulnerability.
Any other Workarounds: None
SQL Server Buffer Overrun Vulnerability:
This vulnerability exists in SQL Server function that allows authenticated user to gain elevated control over the system.
Microsoft has not received any information from customers or other users stating that their system is exploited using this vulnerability and information regarding this vulnerability was brought up through responsible disclosure.
Mitigation Factor: Users with database access can exploit this vulnerability. With SQL Server 2005, services by default run on non-admin accounts. Also SQL Server 2005 prompts for a domain account for services.
Any other Workarounds: None
Are we affected?
We can use Microsoft Baseline Security Analyzer (MBSA 2.1) to determine the vulnerabilities in the System. MBSA 2.1 detects these vulnerabilities and reports of any other missing security updates too.
Download URL:
Deployment Plan and Known Issues:
Deployment Instructions are available in http://www.microsoft.com/technet/security/bulletin/MS08-040.mspx.
Download links and impact instructions for SQL Server
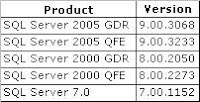
Verification after Installation: Executing the query “Select @@version” should result with the version number given below.
Also the information can be found in the log file on the directory listed below. SQL Server 2000 - %WINDIR%\SQLHotfix SQL Server 2005 - %PROGRAMFILES%\Microsoft SQL Server\90\Setup Bootstrap\LOG\Hotfix
Known Issues:
There are few known issues with this update as listed below.
1. Dependent services remain in stopped state even though SQL Services are started. We have to check and verify that all dependent services are started.
2. SQL Server services or components that are in disabled state will be updated. This security patch update requires that all services to be enabled and running so that the installer detects them and applies the necessary patches.
3. Upon unsuccessful completion, we need to reboot the system so that the changes are rolled back.
953743 (http://support.microsoft.com/kb/953743/) Supported method for applying updates to SQL Server 7.0
953742 (http://support.microsoft.com/kb/953742/) SQL Server 2000 and MSDE 2000 installers stop dependent services
953741 (http://support.microsoft.com/kb/953741/) SQL Server 2005 installers stop dependent services
953740 (http://support.microsoft.com/kb/953740/) How to identify and enable disabled SQL Server instances in SQL Server 2000
953739 (http://support.microsoft.com/kb/953739/) SQL Server 2005 installers do not update an instance of the SQL Server service that is in a
disabled state.
Other Points to Ponder:
This patch is included in SP3 of SQL Server 2005 which is scheduled to release in Third Quarter of 2008. By the time earning freeze is over, we should be having SP3 on which we can schedule to install so that this patch too is applied.
http://blogs.technet.com/dataplatforminsider/archive/2008/04/15/sql-server-2005-sp3-coming-soon.aspx
http://blogs.technet.com/beatrice/archive/2008/04/16/sql-2005-sp3-announced.aspx
http://blogs.technet.com/dataplatforminsider/archive/2008/01/25/microsoft-sql-server-2008-roadmap-clarification.aspx







No comments:
Post a Comment